When a rising Fraud-as-a-Service (FAAS) phishing kit makes it into mainstream media, it’s usually a sign that it has reached a scale and level of sophistication that should alarm cybersecurity professionals.
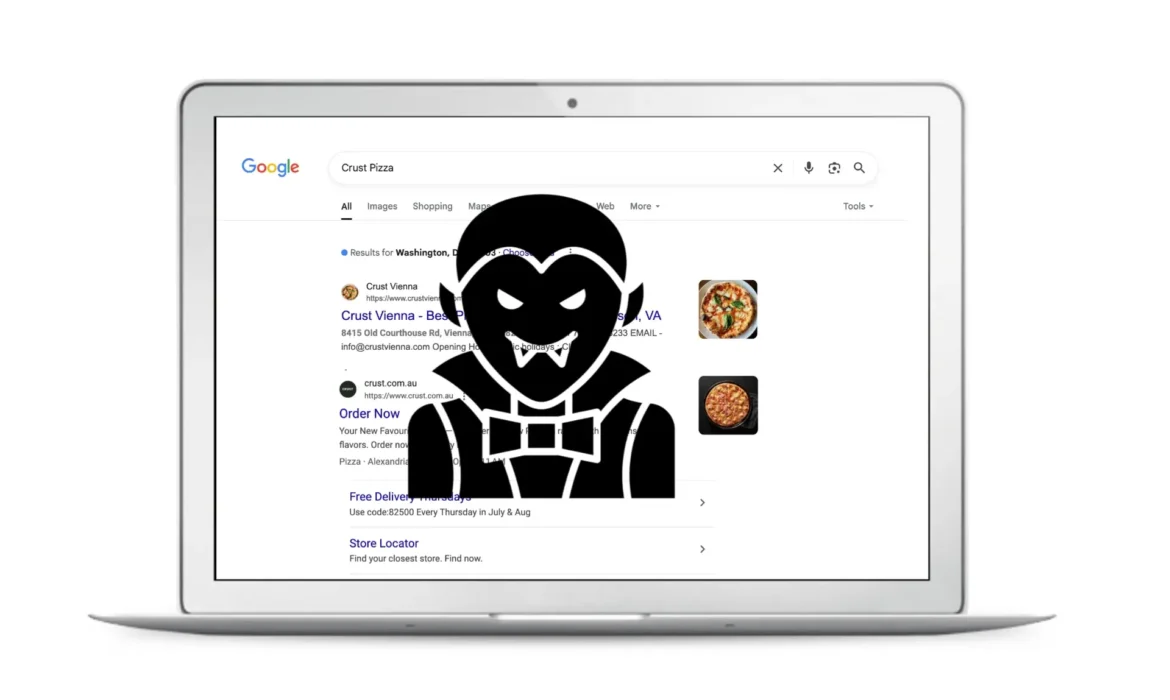
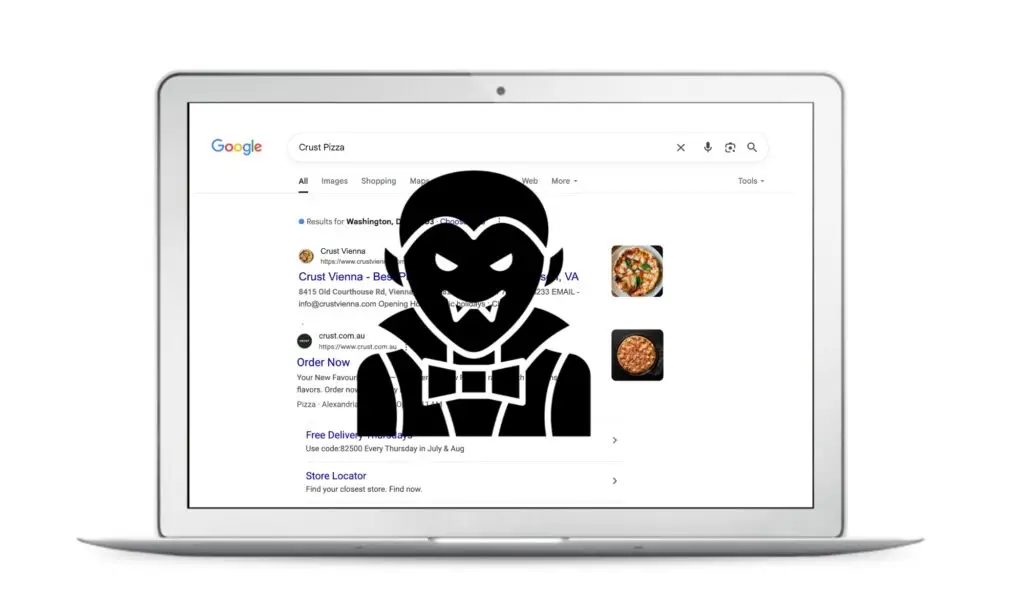
The ABC recently reported on a phishing kit known as Darcula. In the story, a man from Sydney searched for his favourite takeaway—Crust Pizza—on Google. He clicked on the first result, a sponsored ad, and unknowingly landed on a perfect clone of the Crust Pizza website. What should have been a $20 dinner turned into a $570 scam. We have blogged on this phishing kit in the past, which are largely used as the infrastructure behind fake shops.
In this blog we take a look at Darcula, how it works and how you can protect your customers.
What is Darcula?
Darcula is a rapidly growing Phishing-as-a-Service (PhaaS) operation, built to help cybercriminals launch highly convincing phishing campaigns at scale—with minimal effort or technical skill required.
This kit stands out because it combines perfectly cloned websites with multiple delivery channels, including Google Ads, Meta (Facebook/Instagram), and iMessage, to drive unsuspecting users into handing over their personal and financial details.
How Darcula Works
- Google Ads & Meta Ads Exploitation Darcula operators pay for sponsored ad placements on platforms like Google and Meta, allowing fake sites to appear at the top of search results or user feeds. Victims believe they’re clicking a trusted brand, but instead land on a perfect clone controlled by scammers.
- iMessage Abuse Darcula uses iMessage to send phishing links directly, bypassing traditional SMS filtering by telcos. Because iMessage operates over the internet, these malicious messages often avoid detection and reach the inbox unfiltered.
- Turnkey Criminal Infrastructure The Darcula kit allows attackers to mimic major brands like banks, telcos, and courier companies. Its cloned pages look identical to the real ones, making it nearly impossible for the average user to spot the difference.
- Global Targeting, Local Customisation With support for over 100 countries, Darcula localizes the language, design, and brand assets based on the target’s region—making scams feel even more legitimate.
- Fast-Moving, Hard to Trace It uses rapid domain rotation via bulletproof hosting or services like Cloudflare, along with anti-bot and anti-researcher evasion techniques, making takedowns difficult and detection slower.
- Chinese-Language Origins The backend panels, documentation, and community support for Darcula are primarily in Simplified Chinese, linking the operation to Chinese-speaking cybercriminals and Telegram groups trading in phishing tools.
Perfect Clones - Hoka case study
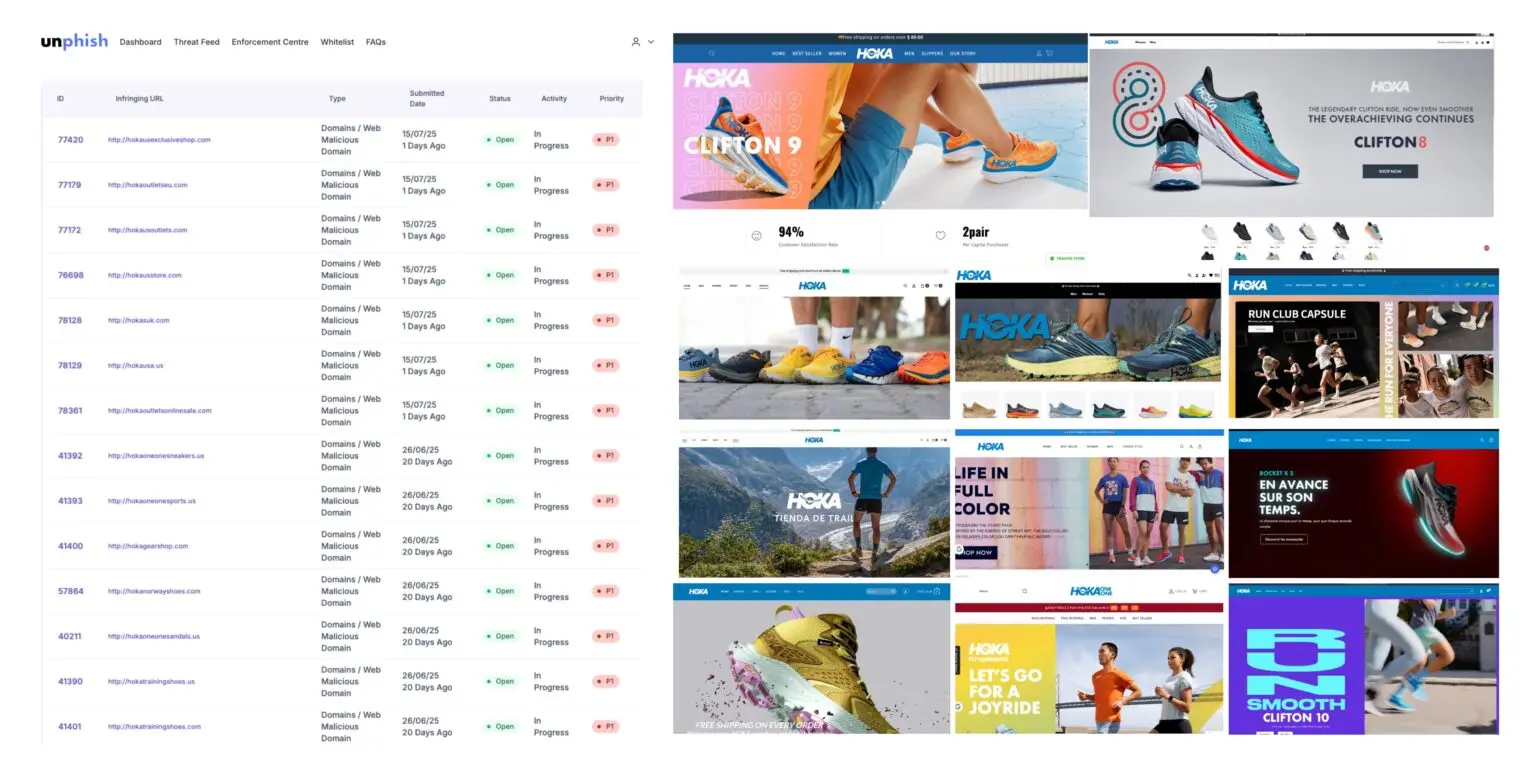
We’ve been tracking a surge in perfect clone websites targeting Hoka, a popular global shoe brand, which appears to be a frequent victim of Fraud-as-a-Service (FaaS) operations like Darcula. We have discovered hundreds of cloned hoka websites, across multiple regions. New sites pop up daily, emphasising the ease and speed that clone sites can be deployed.
These phishing sites are high-quality replicas of the official Hoka website, often with only subtle variations depending on the region they are targeting. Content is localised and cybercriminals continually spin up new domains, frequently rotating URLs to avoid detection. Many of these sites are hosted using Cloudflare or bulletproof infrastructure, and registered through domain name Registrars that offer ultra-cheap first-year domain registrations, making mass deployment both fast and cost-effective.
In Hoka’s case, some of these fraudulent sites have remained live and resolving for months. Worse still, many rank in Google’s organic search results in target countries, while others are actively promoted through Google Ads campaigns—increasing their reach and likelihood of tricking consumers.
How to Defend Against Darcula and Advanced Phishing
Phishing kits like Darcula have made impersonation fast, scalable, and incredibly convincing. Defending against them requires smarter, faster solutions. Here’s how:
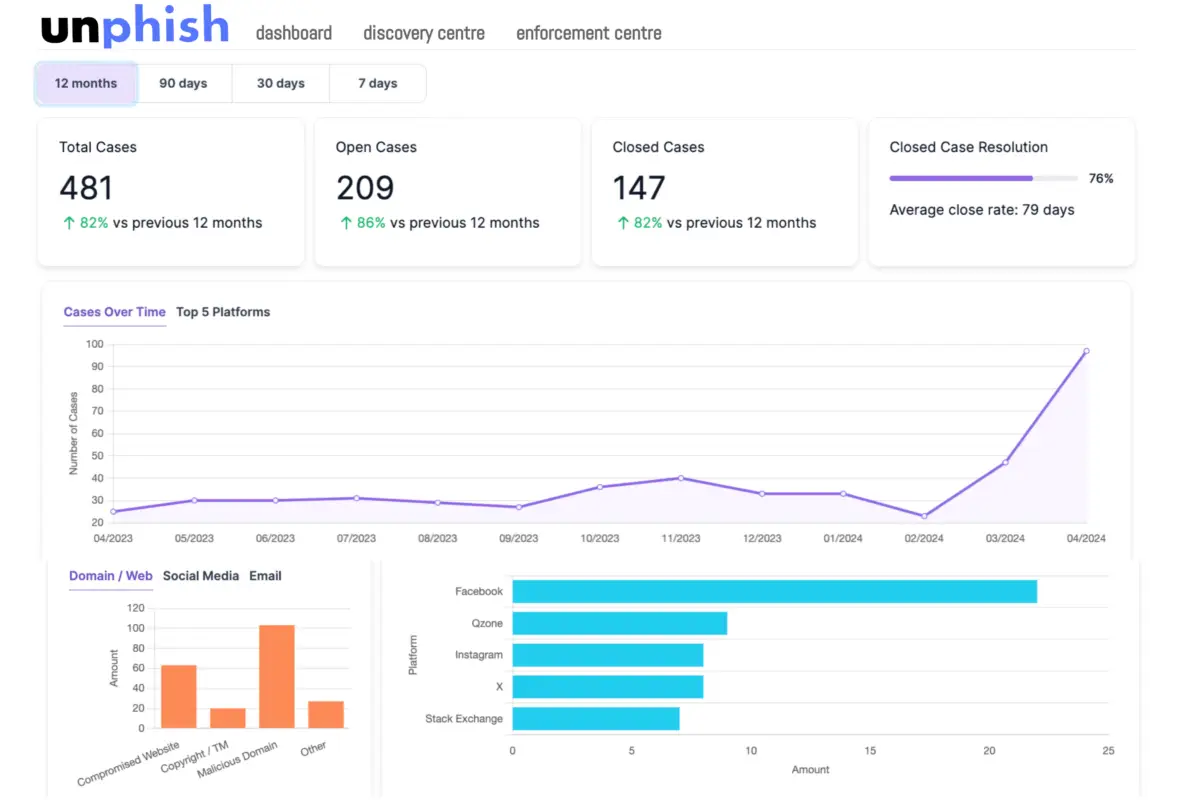
Real-Time Detection and Disruption: Brand monitoring tools like Unphish monitors domains, threat feeds, and web infrastructure to detect phishing sites as they go live—enabling fast enforcement before users are exposed.
Decoy Credential Injection: Some systems fight back by submitting fake credentials to phishing forms, helping identify and trace threat actors. This tactic is emerging but shows promise in disrupting fraud.
Rapid Takedown: When multiple phishing sites share the same host or registrar, Unphish enables bulk enforcement, allowing takedown notices to be issued across entire clusters of malicious domains in one action. This significantly reduces response time and increases takedown success rates—especially against large-scale campaigns like Darcula.
Stay Alert: It’s Not One and Done: Unfortunately, defending against clone attacks isn’t a set-and-forget task. Once cybercriminals profit from your brand, they rarely stop. Attacks tend to come in waves—making ongoing vigilance and continuous detection essential to stay ahead of the threat.
Unphish is built to detect, disrupt, and take down Clone phishing threats
Act quickly & at scale. If you’re facing clone sites, impersonation, or ad-based scams, it’s time to get proactive.
About brandsec
brandsec is a team of highly experienced domain name management and online brand protection experts. We provide corporate domain name management and brand enforcement services, helping brands eliminate phishing platforms across the internet. Supporting some of the largest brands in the region, we offer innovative solutions to combat threats across multiple industries.

Edward Seaford
Product & Enforcement Director
Ed brings over two decades of experience in domain management, brand protection, and phishing defence. At Brandsec and Unphish, he drives the technology and partnerships while leading with a people-first approach.