
FraudOnTok Scam: 10,000+ Fake Websites Hijacking Trust
FraudOnTok Key Takeaways (TLDR)

Cloned Websites 10,000+ impersonation websites identified mimicking TikTok Shop, Wholesale, and Mall

Domains at the heart of the scam Campaign relies on cheap domains (.top, .shop, .icu, etc.) for mass deployment

Deployed Fake Ads on Facebook & Tiktok Fake Facebook ads and AI-generated TikTok videos impersonating influencers

Social Engineering WhatsApp/Telegram outreach to engage victims

5,000+ malicious app download URL detected, distributing trojanized TikTok-style apps

SparkKitty Trojan embedded in fake TikTok apps exfiltrates credentials, device data, images, crypto wallet seed phrases

Global expansion – though TikTok Shop is official in only 17 countries, scams are spreading worldwide

Trojan harvest TikTok credentials – Google OAuth tokens, and crypto wallet details, enabling device compromise
FraudOnTok Introduction
TikTok Shop is growing quickly, and with that growth comes risk. TikTok Shop is not officially available in Australia yet, but a phased rollout is expected within late 2025. A worrying report by CTM360 identifies, what Australian brands and consumers can expect. Specifically, they identify a campaign called FraudOnTok (also referred to the TikTok Shop Scam), which is a large-scale scam targeting both TikTok users and brands. Unlike isolated phishing attempts, this campaign operates at scale, leveraging multi-channel infrastructure, and has already spun up tens of thousands of fake websites designed to trick people into handing over money and personal information.
For brands, the problem isn’t just the loss suffered by individual victims, it’s the reputational damage when customers believe your name or product was tied to a scam… not to mention the resources that get tied up in investigations, communication with impacted customers and law enforcement and then trying to address the problem. This blog tries to make brands aware of the tiktok scam, and provide some practical suggestion to stay one step ahead of it.
What is the TikTok Shop Scam, FraudOnTok?
This TikTok Shop scam is a large-scale fraud campaign that targets both shoppers and affiliate participants. Scammers set up fake TikTok Shop sites and apps to lure victims with heavily discounted products or fake commission offers.
Buyers are tricked into paying through untraceable methods like cryptocurrency or cash collection, while affiliates are pressured to “top up” fake wallets in the hope of future payouts that never arrive.
At the same time, phishing pages and trojanised apps steal login credentials and hijack accounts.
The ultimate goal is simple: to exploit consumer trust and TikTok’s affiliate ecosystem for direct financial gain, made harder to reverse by the use of crypto and other unprotected payment channels.
How FraudOnTok works?
The FraudOnTok scam relies on a web of infrastructure designed to look legitimate while funnelling victims into fraud. It begins with domain names: scammers register thousands of lookalike sites that mimic TikTok Shop, using typosquatted URLs and cheap hosting to build convincing clones. These domains host phishing kits that capture logins, payment details, and personal information.
Traffic is driven to these sites through fake ads on TikTok and Facebook. Many of these ads use AI-generated influencer videos that look like real promotions, offering steep discounts or limited-time deals to entice users to click through. To build further credibility, scammers set up bogus social media accounts that pose as influencers or TikTok affiliates. These profiles make the scam appear more authentic and encourage users to engage.
Once a victim shows interest, they are often steered into private channels such as WhatsApp, Messenger, or Telegram. In these chats, scammers send direct links to phishing sites or push downloads of a fake TikTok Shop app. The app is loaded with spyware, such as the SparkKitty malware, which can steal account credentials, crypto wallet details, and other sensitive information.
Each of these elements – domains, clone sites, ads, fake profiles, and private messaging, work together as part of a coordinated lifecycle. The goal is always the same: disguise the scam long enough to steal data or money, then cash out through cryptocurrency payments or the resale of stolen information.
Scam Stages
Using a framework adapted from MITRE, CTM360 researchers have mapped the scam into seven key steps: resource development, evasion, trigger, distribution, target interaction, motive, and monetization. These phases show how scammers set up their infrastructure, disguise it, lure victims with incentives, spread it through ads and social channels, capture interactions, steal information, and ultimately cash out.
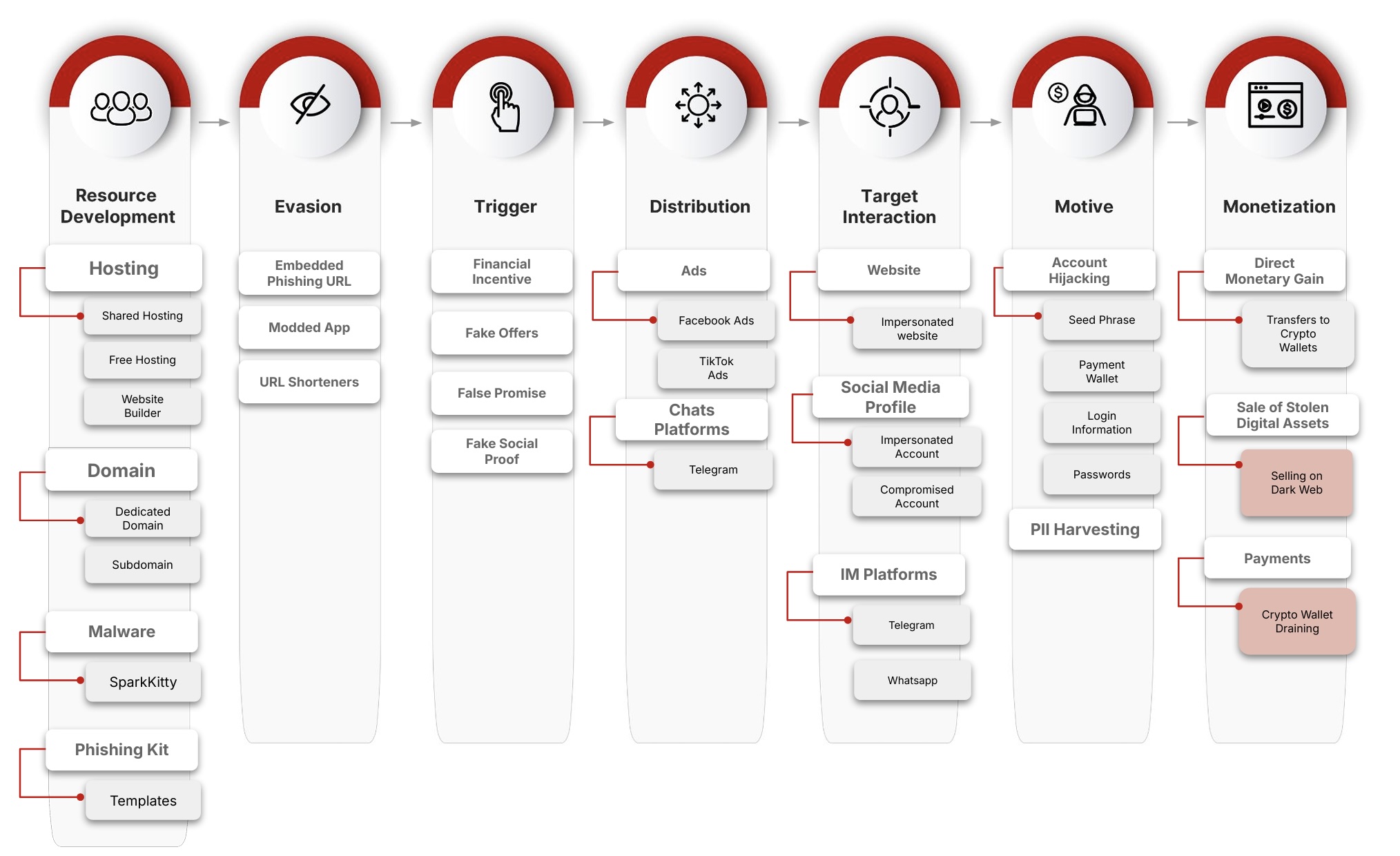
Tiktok Shop Scam Infrastructure
Domain Names were at the centre of the scam
Domain names sat at the centre of the FraudOnTok scam. Threat actors registered thousands of lookalike domains using cheap extensions like .top, .shop and .icu, designed to mimic TikTok Shop, TikTok Mall and TikTok Wholesale. These sites acted as phishing portals to steal logins and payment data, and as distribution points for trojanised apps that installed the SparkKitty spyware.
Many domains also doubled as command-and-control servers, hard-coded into the malware to receive stolen credentials and device data. Others hosted fake affiliate dashboards, tricking victims into depositing cryptocurrency that was siphoned straight to attacker wallets.
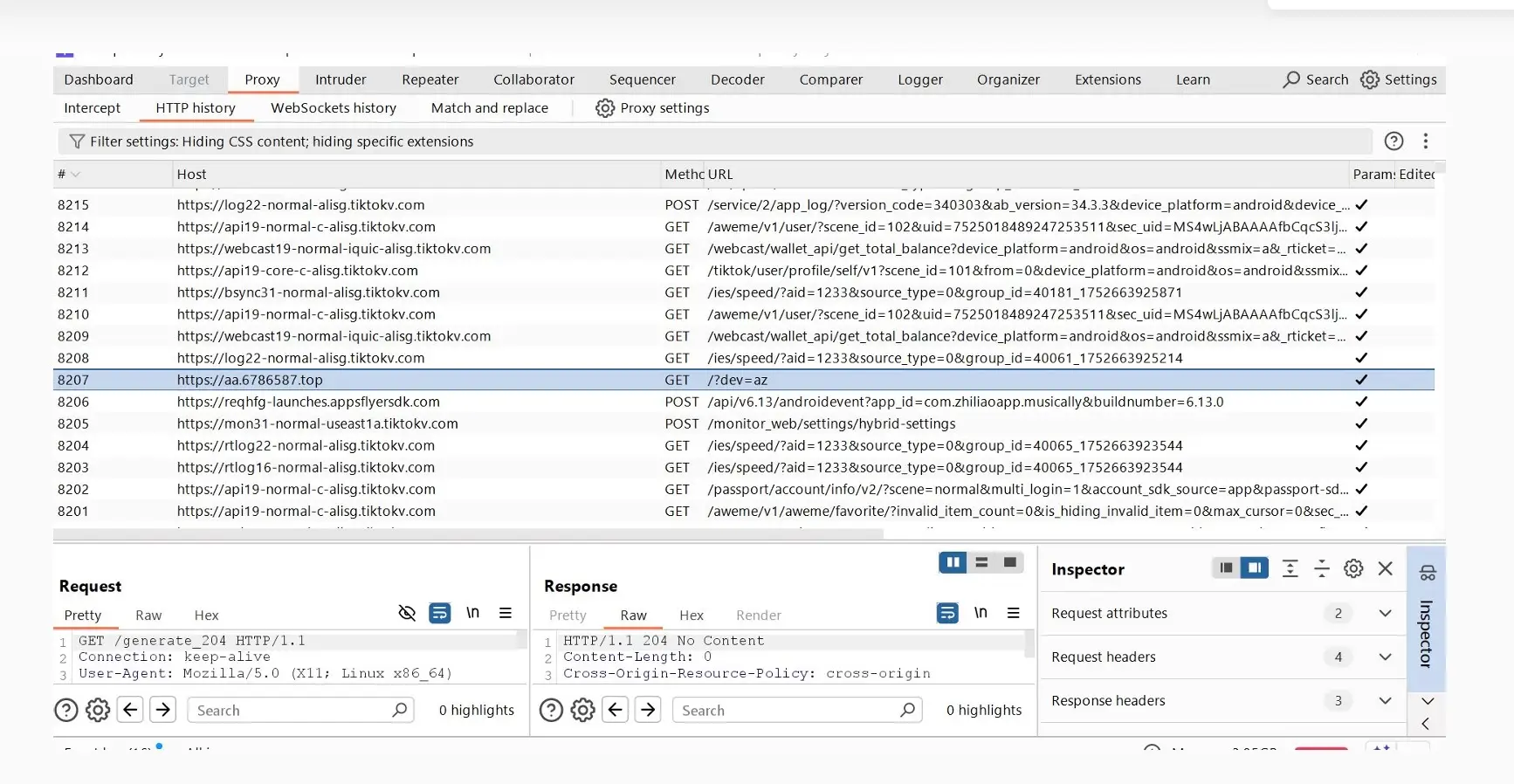
This screenshot shows how FraudOnTok scammers used fake domains to blend malicious traffic with legitimate TikTok communication. While most requests point to genuine TikTok infrastructure (tiktokv.com), one stands out — aa.6786587.top. This is a spoofed command-and-control domain, hard-coded into the SparkKitty malware, designed to capture stolen data and send attacker instructions.
Fake Website / Phishing Templates
With over 10,000 fake websites identified, three primary phishing templates were used, all crafted to mimic different aspects of TikTok Shopʼs commercial ecosystem specifically TikTok Shop, TikTok Wholesale, and TikTok Mall. These phishing templates are used to lure users into depositing cryptocurrency on fraudulent storefronts, leveraging fake product listings and urgency tactics.
Images: credit CTM360
Separately, a distinct malware-based template was also identified, masquerading as a professional Tiktok shop affiliate participants management platform. This variant encourages users to download a malicious App, which is designed to hijack accounts, steal sensitive information, and potentially enable persistent device compromise. While the lures differ, both attack paths exploit user trust in TikTok Shopʼs brand and interface to maximize impact.
Images: credit CTM360
Fake TikTok and Facebook Profiles and Ads
Scammers copy the look and feel of real TikTok Shop activity by running fake ads, creating bogus profiles, and using AI-generated content to lure victims. They push out deceptive promotions on TikTok and Facebook, often featuring AI-made videos that look like genuine brand campaigns but promise unrealistic discounts.
Alongside this, they set up fraudulent influencer or affiliate accounts that appear credible on the surface, giving the scams more legitimacy and drawing users toward counterfeit TikTok Shop pages where malware or fraud is waiting.
Instant Messenger deployed in the scam
Bad actors exploited instant messaging platforms like WhatsApp and Telegram to push the FraudOnTok scam. After luring victims with fake ads or spoofed TikTok Shop sites, scammers moved conversations into private IM chats. There, they posed as TikTok affiliates or support agents, sending direct phishing links, QR codes, and malicious app files. Because IM channels are encrypted and unregulated, these interactions appeared personal and trustworthy, making it easier for scammers to pressure victims into downloading trojanized apps or transferring cryptocurrency.
How Victims were ultimately scammed
Victims were drawn in through fake TikTok Shop websites, AI-generated ads, and bogus influencer profiles that closely mimicked real promotions. Once engaged, they were tricked into making purchases for products that never existed, paying through untraceable methods like cryptocurrency or cash collection.
Others were persuaded to “top up” fake affiliate wallets under the promise of future commissions, which never materialised. At the same time, phishing pages and trojanised apps were used to steal login credentials and hijack accounts, allowing attackers to drain crypto wallets and harvest sensitive personal data.
How Brands Can Avoid Being Caught Up in These Scams
The best defence is visibility and speed of response. Scams like this often begin with lookalike domains, fake social profiles, and fraudulent ads — all things that can be detected early with the right monitoring in place. Platforms like Unphish can detect these issues early and piece them together.
It is recommended that brands actively:
- Monitor new domain registrations that contain brand names or close variations, often the first sign of a scam campaign.
- Detect and remove phishing sites before they can capture customer data or money.
- Track fake social media profiles and fake ads that impersonate brands or affiliates.
- Automate takedowns so fraudulent sites and accounts are removed quickly, reducing customer exposure.
- Provide evidence and reporting to help brands communicate clearly with customers and regulators when scams occur.
By combining monitoring, detection, and enforcement, brands can avoid being blindsided by campaigns like FraudOnTok. While no brand can stop criminals from setting up fake sites, having the ability to find and shut them down quickly is the difference between an isolated incident and a reputational crisis. Tools like Unphish can automate the detection, enforcement and intelligence to piece these types of scams together.
Further Reading: CTM360, FraudOnTok – The SparkKitty Drop on TikTok Shops, August 2025.
About brandsec
brandsec is a team of highly experienced domain name management and online brand protection experts. We provide corporate domain name management and brand enforcement services, helping brands eliminate phishing platforms across the internet. Supporting some of the largest brands in the region, we offer innovative solutions to combat threats across multiple industries.

Edward Seaford
Product & Enforcement Director
Ed brings over two decades of experience in domain management, brand protection, and phishing defence. At Brandsec and Unphish, he drives the technology and partnerships while leading with a people-first approach.