Hidden in Plain Sight: 6 Ways Phishing Sites Avoid Detection
Phishing websites have become far more sophisticated than the basic spoof pages we saw a few years ago. As security experts improve detection and website monitoring techniques, attackers adapt just as quickly. It’s a constant game of cat and mouse. Increasingly, phishing operators are turning to technical tricks – some simple, others quite clever to avoid being found by traditional monitoring tools.
These tactics don’t rely on advanced malware or complicated infrastructure. Instead, they take advantage of how most security systems work: automated, rules-based, and often predictable. By exploiting blind spots things like how crawlers behave or where scans originate from phishing sites can quietly collect sensitive information while staying out of sight from security teams.
Here are five tactics we frequently see in the wild, along with why they work and how to counter them.
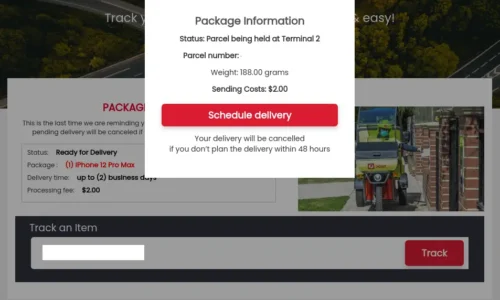
1. Noindex, Nofollow – Simple yet effective.
Some security teams rely heavily on Google’s API or other indexed sources to pick up phishing URLs. But that assumes the phishing site wants to be indexed. Many don’t.
Bad actors often add meta tags like <meta name="robots" content="noindex, nofollow"> to their pages or tweak their robots.txt file. This tells legitimate bots not to index or follow the page. Most reputable crawlers—Google included—respect these instructions.
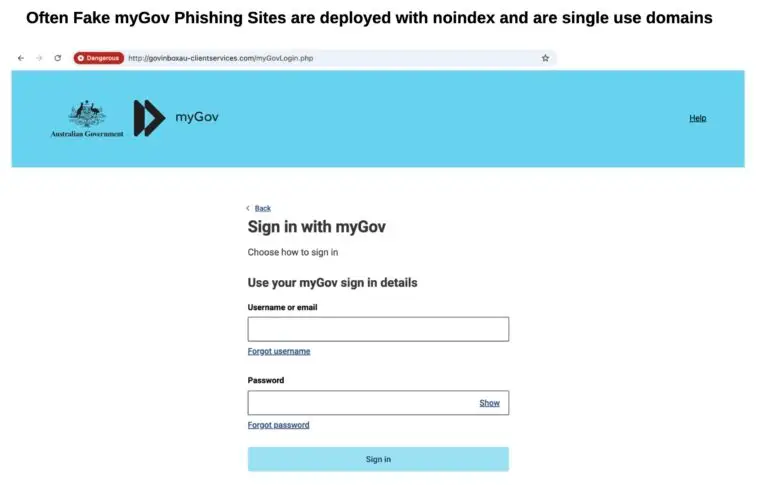
And that’s the problem. While defenders follow the rules, attackers use that against them. Pages with these directives may never show up in indexed search results or automated tools that rely on passive discovery. Unless your monitoring systems explicitly ignore these settings (or use alternate discovery methods), you’ll miss them completely.
2. Cloaking and User-Agent Filtering
This one’s sneaky—and surprisingly common. Phishing pages can detect what type of visitor is hitting them. If the user-agent or IP address looks like it belongs to a scanner, bot, or security provider, the site might show a blank page or redirect to a legitimate site. But if it’s a regular user clicking a phishing link in an SMS or email, they’ll see the full spoofed login experience, branding and all.
We’ve seen this often in toll scams and invoice fraud—anywhere the attacker wants the site to remain hidden from prying eyes until the damage is done.
Standard crawlers miss these sites entirely. To catch them, you need smarter tooling that rotates user-agents, uses headless browsers, or mimics human interaction. Human analysts also play a role spotting odd patterns in domain registrations or sniffing out deceptive redirects the tools can’t always catch.
3. Geo IP Evasion
Phishing sites don’t need to be visible to everyone just the people they’re targeting. Attackers often set up geo-based filtering so that only users from specific countries (e.g. Australia, Southeast Asia) can access the content. Everyone else particularly IPs from cybersecurity vendors or servers in the US or Europe gets blocked or redirected. This tactic is particularly popular among fake shops and ecommerce scams.
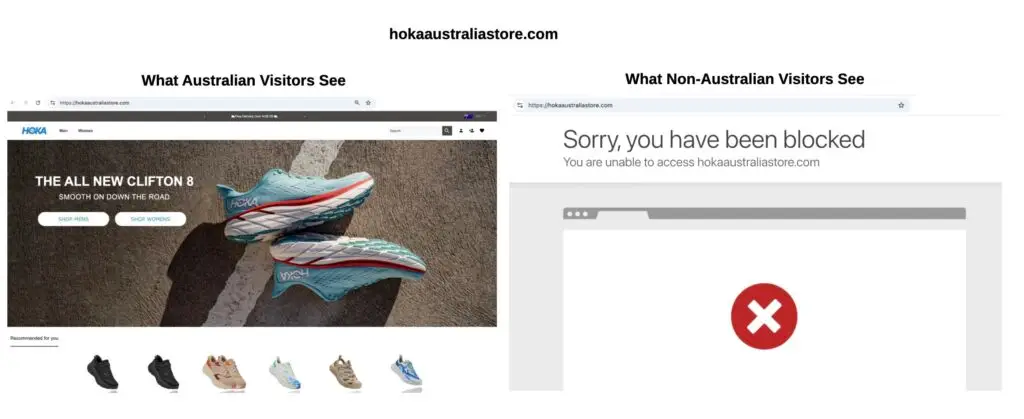
This technique helps attackers fly under the radar of global monitoring infrastructure. A scan from a US-based server might see nothing, while a victim in Brisbane sees the fake login page.
To get around this, monitoring platforms need distributed scanning capabilities think residential proxies, region-specific cloud instances, or local analysts manually checking URLs from within the targeted region
4. Hosting on Compromised Sites
Registering a new domain for phishing can be risky. It’s easier, and sneakier, to hack into an existing, legitimate site and stash your phishing page in a hidden folder. The rest of the site stays untouched, so at a glance (or to an automated scanner), it looks clean.
We see this often with small business websites, community groups, or outdated WordPress installs. The phishing page might sit quietly at randomstore.com/.cba/login/ and go unnoticed for weeks.
The advantage for the attacker? The domain already has a good reputation, valid SSL, and isn’t flagged in threat feeds. Plus, takedown becomes a longer process since it involves the actual website owner or hosting provider, who may not even know they’ve been compromised. Sometimes convincing the owner that you are trying to help them is met with suspicious which further delays the takedown process.
Detection in these cases usually comes down to pattern recognition, content analysis, and looking beyond just domain reputation.
5. Single-Use or Expiring URLs
Some phishing links are designed to disappear after a single click or a short window of time. Once the victim visits the site, it either shows a 404 error or redirects to a harmless page.
These are especially tricky when used in SMS or WhatsApp scams. By the time anyone reports the link or a security team gets involved, the payload is gone. Traditional URL scanners won’t pick up anything suspicious, and there’s no evidence left to act on.
To catch this kind of attack, you need systems that can monitor and react in real time (including collecting evidence such as screenshots, meta data etc). That might include browser-based sensors, link capture tools, or alerting mechanisms tied to inbox or SMS activity. Speed is everything—if you’re not scanning the link while it’s active, you’re already too late.
Remove Phishing Content Quickly and Effortlessly with Unphish
Experience best in class detection and removal of web based phishing platforms through a local and expert team.
5. Cloaked Phishing Login Pages
Bad actors often disguise their phishing infrastructure by placing fake login pages that mimic trusted platforms such as banks, email providers, or social networks. Rather than delivering malware, these cloned forms act as a shield, giving the site a veneer of legitimacy while tricking users into entering their credentials.
By hiding behind a login prompt, attackers reduce the chance of automated scanners flagging the site. Security tools may only see a harmless form, while in reality the page is designed to harvest usernames, passwords, and other sensitive details. This tactic allows phishing sites to remain online longer, evade detection, and capture valuable credentials before takedown.
Stay Aware of the tricks
Phishing operators aren’t always using bleeding-edge tactics, but they are smart and opportunistic. Most of the methods outlined above work because they exploit the assumptions built into many detection systems. That’s why the best defense involves a mix of automation, regional awareness, and experienced analysts who know what to look for.
If your monitoring strategy assumes attackers will play fair, it’s probably time for a rethink.
About brandsec
brandsec is a team of highly experienced domain name management and online brand protection experts. We provide corporate domain name management and brand enforcement services, helping brands eliminate phishing platforms across the internet. Supporting some of the largest brands in the region, we offer innovative solutions to combat threats across multiple industries.

Edward Seaford
Product & Enforcement Director
Ed brings over two decades of experience in domain management, brand protection, and phishing defence. At Brandsec and Unphish, he drives the technology and partnerships while leading with a people-first approach.