
Registry Lock Prevents Domain Name Hijacking
What is Domain Name Hijacking?
Domain name hijacking, aka DNS Hijacking, is when an unauthorized third party, often a hacker, gains control of a company’s domain name portal and seizes control over their DNS system, enabling them to make unauthorized changes and transfers.
Once the unauthorised third party gains access to a domain name account, a common tactic is to amend the Name Server records to redirect Internet traffic through external hosts.
DNS hijacking can be used for pharming (in this context, attackers typically display unwanted ads to generate revenue) or for phishing (displaying fake versions of sites users access and stealing data or credentials). Often hackers will attempt to transfer the domain name to their own Registrar or modify zone files such as the MX record to receive all of a business’ incoming mail.
Between March and September 2024, security researchers analysed over 29 billion DNS records across multiple regions and sectors. Within this enormous dataset, they identified 6,729 confirmed cases of DNS hijacking, averaging 38 compromised DNS records every single day. These weren’t isolated incidents, many were linked to coordinated campaigns targeting financial services, government portals, and large-scale consumer platforms. In some cases, attackers maintained control of hijacked records for weeks before detection, silently redirecting traffic to phishing sites or malware payloads. The study highlighted that even with advanced monitoring, the speed and persistence of these attacks mean they often evade detection until significant damage has been done.
Case Study: Malaysia Airlines Main Site Hijacked by Cyber Caliphate
On January 26, 2015, Malaysia Airlines’ website was hit by a DNS hijacking attack carried out by the hacker group Lizard Squad, styling themselves as the Cyber Caliphate. Visitors to malaysiaairlines.com were redirected to defaced pages—first showing the taunt “404 – Plane Not Found” (a jab at the missing MH370) with “ISIS will prevail,” and later replaced with the Lizard Squad logo.
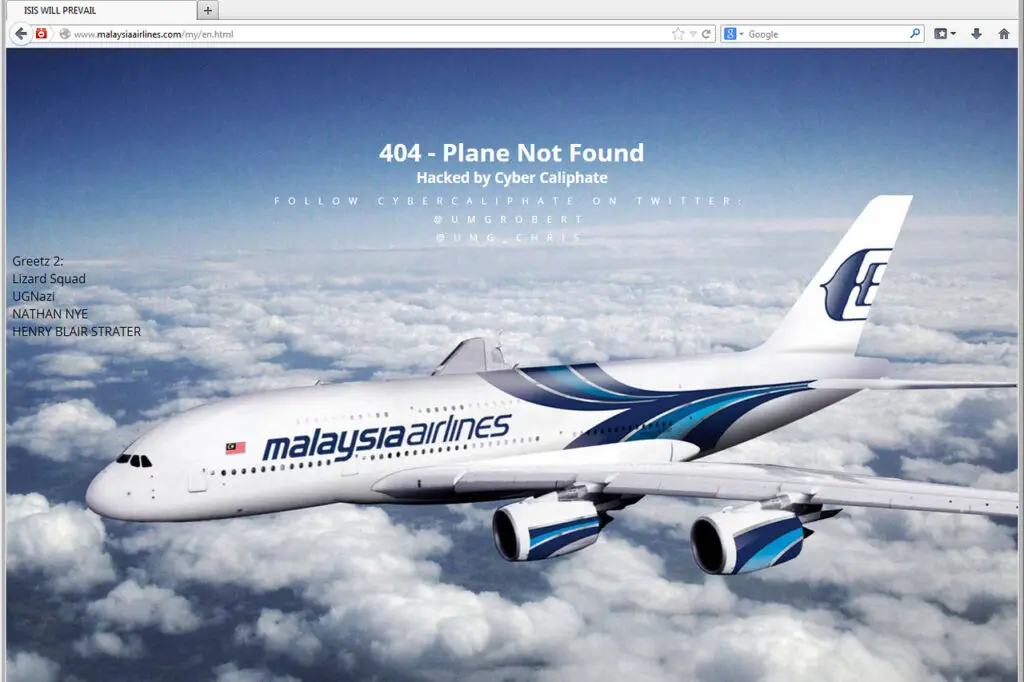
The attackers claimed to have accessed passenger booking data and threatened to leak it, though Malaysia Airlines stated that its servers were not breached, bookings were unaffected, and customer data remained safe. The incident, resolved within roughly 22 hours, highlighted how DNS infrastructure can be exploited to damage a brand without directly hacking its internal systems.
How would Registry Lock have prevented this hijacking?
Registry Lock is a security measure offered by domain registries to protect high-value domains from unauthorized changes. It works by placing a lock at the registry level on critical settings, such as DNS records, nameservers, and contact details, so that even if a registrar account is compromised, no changes can be made without passing a strict, manual verification process. This usually involves out-of-band authentication, such as phone calls, PIN codes, or multi-party approval, to ensure only verified and intentional updates go through.
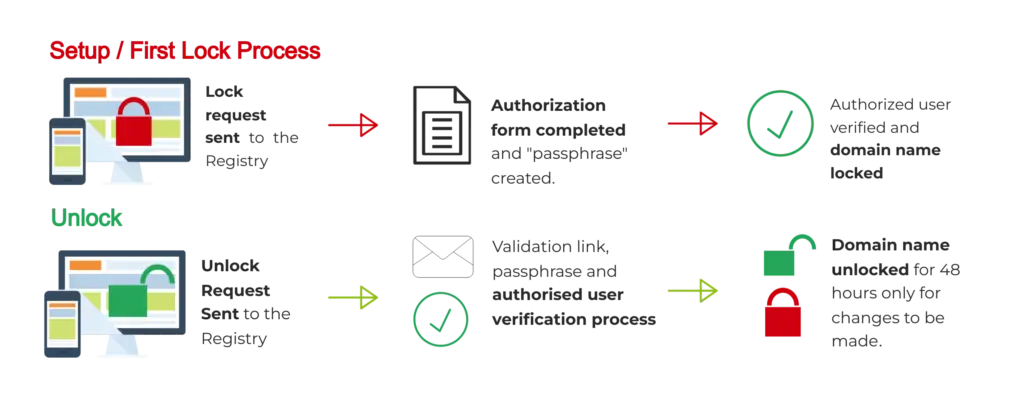
In the case of Malaysia Airlines, the 2015 hijack was achieved by altering the domain’s DNS settings to point visitors to a malicious server. If Registry Lock had been in place, those nameserver changes would have been blocked automatically at the registry. The attackers would have faced an additional, human-verified security layer they almost certainly could not bypass, meaning the DNS redirection,and the associated reputational damage, would never have occurred.
About brandsec
brandsec is a team of highly experienced domain name management and online brand protection experts. We provide corporate domain name management and brand enforcement services, helping brands eliminate phishing platforms across the internet. Supporting some of the largest brands in the region, we offer innovative solutions to combat threats across multiple industries.

Edward Seaford
Product & Enforcement Director
Ed brings over two decades of experience in domain management, brand protection, and phishing defence. At Brandsec and Unphish, he drives the technology and partnerships while leading with a people-first approach.



