Has brand protection kept up with fast moving and large clone website networks? Whether you’re in retail, banking, or government services, attackers can now deploy hundreds of convincing fake websites in hours — complete with stolen branding, payment or credential-harvesting systems, and search-engine-friendly domains. This blog looks at how big the problem has become, why enforcement often struggles to keep up, and what brands can do to stay ahead.
FaaS: an industrial-scale problem across industries
Fraud-as-a-Service (FaaS) packages the tools, infrastructure, and playbook for online impersonation into an on-demand product. Buyers, whether they’re targeting shoppers, bank customers, or citizens, get a ready-made clone site with:
- Full catalogue or service menu (scraped from the legitimate brand)
- Integrated payment or credential-harvesting gateways
- Google-friendly SEO, often boosted by expired domains with existing authority
- Automated SSL certificates to look trustworthy
- Hosting/CDN shielding to hide origin servers and frustrate takedowns
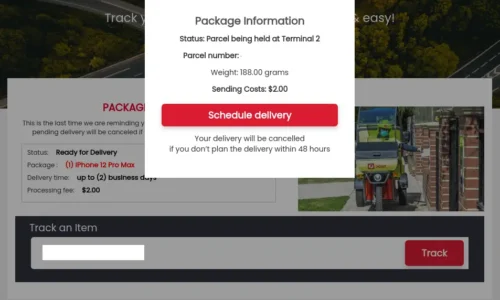
Unlike counterfeit goods on marketplaces, FaaS attacks play out across the open web – targeting retail checkouts, banking logins, utility accounts, and government portals alike.
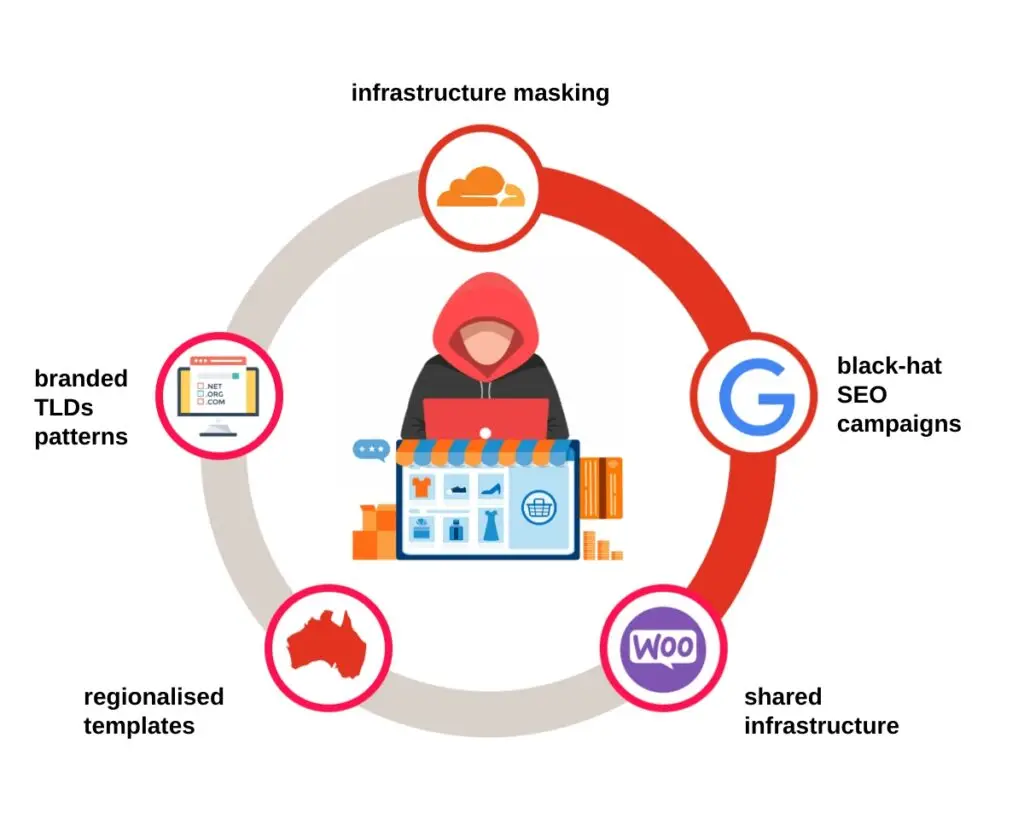
FaaS operations like Bogus_Bazaar, a well documented fake shop operation targeting global retail brands, work a lot like a franchise. The core operators build the backend infrastructure – a content management system, payment capture tools, shipping/order templates, and hosting setup, along with a library of cloned storefront designs. They then rent or sell access to “affiliates,” who customise the fake sites with stolen product images and brand logos, choose from preloaded domain names (often expired ones with existing Google trust), and launch them in bulk. Black-hat SEO and paid ads drive traffic to these sites, while bulletproof hosting and CDNs hide their origins. Payments flow into accounts controlled by the network, or stolen card data is harvested for resale. If a site gets taken down, the kit makes it easy to spin up a replacement within hours – making enforcement a game of whack-a-mole.
In terms of scale of these operation, research tied 75,000 fake shops to one FaaS operation, victimising ~850,000 people worldwide (over a three year period). The same kit was used to impersonate retailers, electronics brands, and even service portals, with losses in the tens of millions – plus industrial scale credential theft. Not all payments were successfully processed, but analysis suggests the group may have attempted to take as much as €50m (£43m) over the period.
FaaS is industry agnostic, if a brand stores customer data of value, it’s a target. Finance, retail, and government services are all in the crosshairs. One sector we’ve tracked closely is shoe and sports apparel. Across multiple brands, we’ve observed thousands of new domains spun up in redirector chains and hosted on rotating infrastructure to evade detection.
An example of a targeted brand is Hoka Shoes, where we’ve identified hundreds of fake “Hoka” sites resolving at any given time. Many follow regionalised templates tailored to specific countries, Australia, Germany, Turkey, and others, right down to currency, language, and local imagery. In fact, we’ve become so familiar with the patterns that we can often identify the specific sub-group behind an attack purely from the template they use.
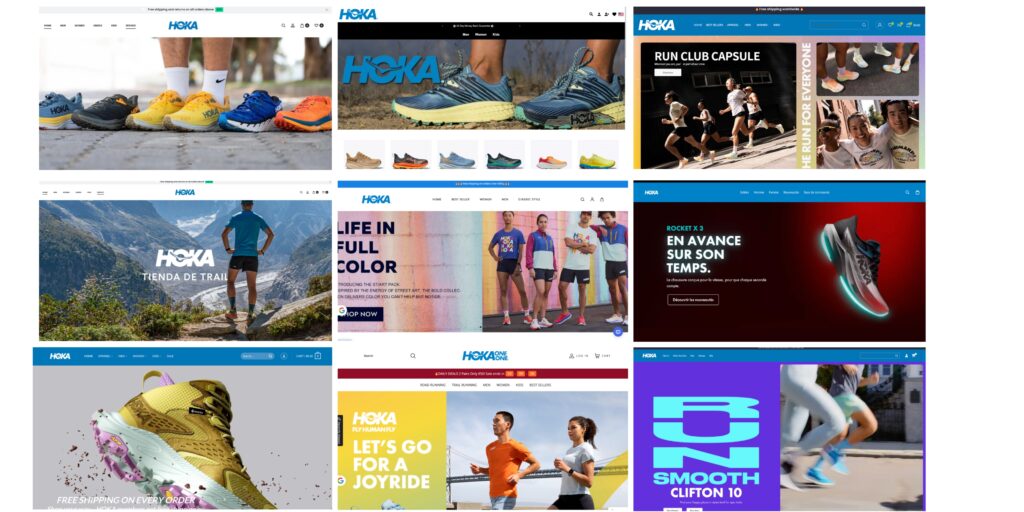
The challenge for brands, such as Hoka, is fighting a decentralised network that uses persistent and black-hat SEO and evasive redirector chains as the primary traffic drivers, not to mention kit reuse + shared infrastructure let operators respawn domains quickly after takedowns.
Is tired brand protection technology keeping up? How do we even the fight?
If we are going to be honest, a lot of brand protection technology is still playing last decade’s game. They are built to spot a knock-off handbags on marketplaces or the occasional phishing page, not to hunt down industrial-scale FaaS networks that can churn out hundreds of clone sites brand protection analysts have had their first coffee. Many brand protection companies talk about using artificial intelligence and other advanced tools to level the playing field, but the decentralised nature of the internet still tilts the advantage toward FaaS operators – and keeps brand protection teams on the back foot. Areas where brand protection falls short in the fight against FAAS operations:
- Detection is slow compared to the speed these FAAS networks can deploy. Most brand protection programs deploy periodic sweeps or set up keyword alerts which simple don’t keep up with how quickly FaaS kits deploy new sites. The time it takes for a domain name to be registered and deployed is minutes. If we look at domain name monitoring as a service – ICANN only provide access to the newly registered domain name data base (CZDS) once every 24 hours, meaning bad actors can register and launch a phishing site many hours before it even becomes discoverable (not to mentioned the processing time to find the infringing domain name). To achieve closer to real-time detection, you need to combine CZDS with other data sources like passive DNS feeds, registrar drop lists, certificate transparency log monitoring, and threat intel or domain monitoring APIs, which overall requires far more infrastructure than the FAAS operations deploying these sites at scale.
- One by one takedowns (or takedowns in isolation) are almost pointless. Talk about a poor use of time and energy. This random and reactive approach to brand protection is getting more and more outdated by the day. By the time a site is spotted, indexed, and reported, the attackers have already deployed 10 more sites. Often bad actors will registered tens to hundreds of domain names at a time using the same Registrar, host, payment gateway provider. killing a single site doesn’t matter if the kit behind it can spawn another hundred in a day. So a strategic and deliberate approach is required. Specifically, identifying and targeting the entire cluster tied to the same infrastructure, registrar, host, CDN, or monetisation pipeline. With this approach you don’t just remove a single phishing page, you disrupt them at a network level.
- Data is scattered: – WHOIS, DNS, CT logs, threat feeds… they’re not always stitched together, so sites sometimes slip through. This is where a smart detection system, trained specifically on the behaviours and patterns of a known FaaS network, can make a huge difference. By correlating data points across registrant details, name server changes, SSL issuance, hosting patterns, and threat intel, such a system can connect the dots in ways that humans – or off-the-shelf brand protection tools, often miss. But building and maintaining that capability isn’t cheap; it requires sustained investment in technology, data access, and analyst expertise to stay ahead of the threat.
- Policy isn’t keeping up: One of the biggest challenges in fighting FaaS is that policy lag far behind the threat. DNS abuse definitions around “phishing” are often narrow or loosely interpreted, and many registrars take a minimalist approach to enforcement. Fake shops that clearly impersonate a brand will sometimes be ignored because, under current certain Registrars definitions of DNS abuse, proving “fraud” often requires an actual customer complaint or evidence of a phishing email – even if the domain is obviously malicious. It doesn’t take long for bad actors to find the Registrars that are slow to act or have strict evidence requirements. A host-level takedown might pull the site offline temporarily, but FaaS operators are set up for rapid redeployment. Within hours, the exact same kit – product pages, checkout forms, payment integrations can be live again on a new host. Without coordinated action at the domain, hosting, CDN, and payment levels, policy gaps mean enforcement will continue to be inconsistent, reactive, and sometimes easy to sidestep.
Better brand protection: How brands can give themselves the edge against FaaS
Any cyber security professional will attest that FaaS isn’t going away, and waiting for policy to catch up or for existing brand protection tools to suddenly get faster is a losing strategy. If brands want the upper hand, they need to re-engineer their approach so they’re discovering threats earlier, acting on clusters (as opposed to individual cases), and removing the infrastructure that makes these operations possible. Here are some practical steps to give your brand the edge:
1. Shorten the detection window
Don’t rely solely on once-a-day CZDS data or Google. Combine it with multiple data sources such as passive DNS, registrar drop lists, certificate transparency log monitoring, and real-time threat intel feeds. The goal is to spot a domain within minutes of it resolving, not after it’s already ranking in Google.
2. Think in clusters, not URLs
When you find one fake site, look for its siblings. Where there is one, there is likely to be another tonne. Target domains sharing the same registrar, hosting network, CDN, and payment gateway. Cluster-based takedowns make it harder for the network to reappear overnight.
3. Hit the money flow
Without payment processing, most fake shops collapse. Report fraudulent merchant accounts, whether they’re tied to banks, PSPs, or crypto wallets.
4. Stitch the data together
Integrate WHOIS, DNS, SSL, and hosting pattern data so you can track the full footprint of a FaaS network. Invest in systems (or partners) and automated where possible that can connect the dots faster than a human analyst.
5. Create internal muscle memory
Your security, legal, and brand teams should be able to act without hesitation. Build playbooks for common FaaS patterns so every new detection triggers a repeatable, rapid response.
6. Collaborate beyond your brand
Join industry threat-sharing groups or sector-specific ISACs. FaaS groups target multiple brands at once – coordinated reporting increases pressure and makes it harder for them to simply pivot to the next victim.
In summary, FaaS has industrialised online impersonation, giving criminals the ability to launch hundreds of convincing fake sites in hours. Beating FaaS requires shifting from slow, one-by-one takedowns to fast, data-driven, and cluster-based enforcement that targets the entire network – from domains and hosting to CDNs and payment processors. Brands that invest in real-time detection, integrated intelligence, and coordinated action will be best placed to turn the fight in their favour.
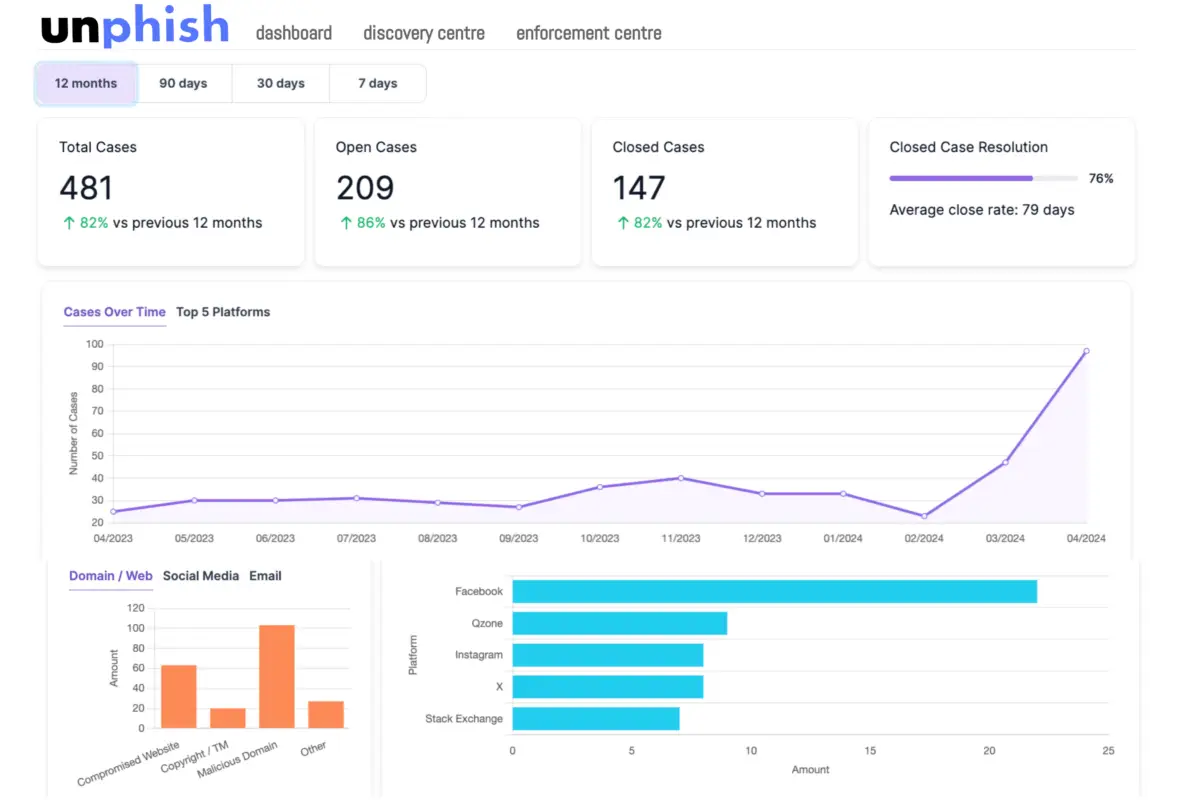
Remove Phishing Content Quickly and Effortlessly with Unphish
Sign up for Unphish for a strategic and best in class takedown solution
About brandsec
brandsec is a team of highly experienced domain name management and online brand protection experts. We provide corporate domain name management and brand enforcement services, helping brands eliminate phishing platforms across the internet. Supporting some of the largest brands in the region, we offer innovative solutions to combat threats across multiple industries.

Edward Seaford
Product & Enforcement Director
Ed brings over two decades of experience in domain management, brand protection, and phishing defence. At Brandsec and Unphish, he drives the technology and partnerships while leading with a people-first approach.